In a crypto ecosystem where transparency has become the norm, Midnight ($NIGHT) positions itself as a bold response to a growing need: privacy without compromising compliance. Developed by Charles Hoskinson, the co-founder of Ethereum and creator of Cardano, this next-generation blockchain uses zero-knowledge proofs to offer what it calls "rational privacy", an approach that allows proving the veracity of information without revealing the underlying data.
But beyond the ambitious vision and the credibility of its founder, what is Midnight really worth from a technical, financial, and security standpoint?
Thanks to Kryll X-Ray, we've put the project under scrutiny: finances, fundamentals, security, on-chain data, smart contracts, social networks... Here's the complete audit of this highly anticipated newcomer.
What is Midnight ($NIGHT)?
Midnight is a fourth-generation blockchain built around the concept of "rational privacy," which uses a dual-state ledger architecture to combine public transparency and private data management. Unlike traditional blockchains that expose all transactions, Midnight allows applications to validate sensitive data through cryptographic proofs while remaining auditable on-chain.
The protocol relies on zero-knowledge proofs (ZK proofs), which allow one party to prove that a statement is true without revealing the sensitive information underlying it. This technology is natively integrated into Midnight's architecture, unlike other blockchains that have attempted to add privacy as an afterthought.
Key points of Midnight:
- Dual-state architecture (public state + private state)
- Use of ZK SNARKs for privacy
- Compact smart contract language based on TypeScript
- Programmable selective disclosure
- Compatible as Layer 1 or Layer 2
Privacy-first vs Transparency-first: the new blockchain paradigm
The blockchain industry faces a fundamental tension: how to reconcile decentralized transparency with the legitimate need for privacy for businesses and individuals?
Public blockchains offer transparency but expose sensitive business data, making them unsuitable for institutional use cases. Conversely, private blockchains create regulatory compliance issues.
Midnight positions itself as a third way:
- Selective disclosure: Users choose what data to share, when, and with whom
- Built-in compliance: Privacy becomes a starting point for compliance, not an obstacle
- Privacy by design: Unlike projects like Monero or Zcash that have encountered regulatory problems, Midnight integrates privacy from the design stage while enabling auditability
This approach is particularly relevant for sectors requiring absolute privacy: financial services, healthcare, digital identity, corporate governance.
Developer accessibility: the key to adoption
One of the main obstacles to the adoption of ZK technologies has always been their cryptographic complexity. Midnight uses Compact, a language based on TypeScript familiar to millions of developers, which abstracts the underlying cryptographic complexity.
Advantages for the ecosystem:
- No need for teams specialized in cryptography
- Reduced development cycles
- Significantly lowered barrier to entry
- Easier integration with existing systems
This developer-friendly approach, combined with the partnership with Google Cloud for infrastructure support, positions Midnight for rapid adoption by businesses and mainstream developers.
The X-Ray audit of Midnight ($NIGHT)

Artificial intelligence in the service of crypto is precisely our specialty, but in the other direction: we use it to analyze and audit Web3 projects. Thanks to our Kryll X-Ray tool, every data point, every metric, and every on-chain signal is inspected in depth to offer a clear, objective, and unfiltered view of the project.
Midnight arrives with a strong narrative (rational privacy), a recognized founder (Charles Hoskinson), and promising partnerships (Google Cloud). But as always in crypto, enthusiasm is not enough.
To truly understand the solidity of a project, you have to go beyond the hype and examine the fundamentals, identify weak signals, spot risks, and measure technological consistency. That's exactly what Kryll X-Ray does: every metric, every on-chain movement, and every security point is placed under the microscope.
Financial analysis of Midnight ($NIGHT): massive volumes and controlled dilution
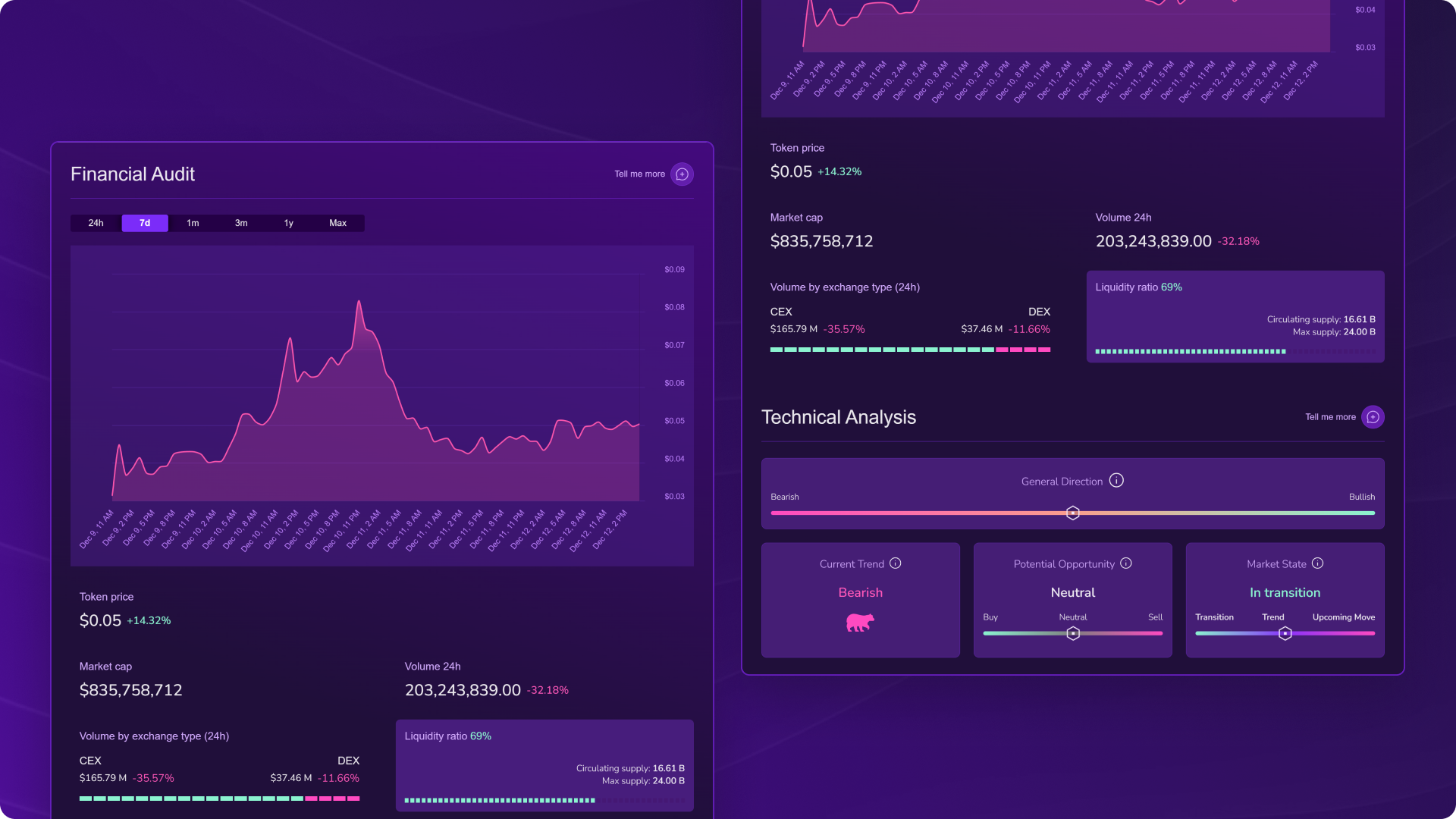
- Token price: $0.05
- Market capitalization: $835,758,712
- 24h volume: $203,243,839 (-32.18%)
- Liquidity ratio: 69%
- Circulating supply: 16.61B
- Maximum supply: 24.00B
👉 To simplify: Midnight displays a solid capitalization of over $835 million with daily volumes exceeding $200 million, proof of sustained market interest. The 69% liquidity ratio is decent, indicating that a large portion of the supply is available, limiting manipulation risks. With 16.61 billion tokens in circulation out of a maximum of 24 billion, approximately 69% of the total supply is already circulating, suggesting moderate future dilution.
Technical analysis of Midnight ($NIGHT): bearish trend but neutral opportunity
- General direction: Bearish
- Current trend: Bearish
- Potential opportunity: Neutral
- Market state: In transition
👉 In summary: The general trend is clearly bearish in the short term, as shown by technical indicators. However, the neutral opportunity suggests that the token is in a transition zone, potentially before a reversal. For investors, this means caution is warranted, but gradual accumulation could be considered in case of reversal signals.
Fundamental analysis of Midnight ($NIGHT): recent project but solid backing
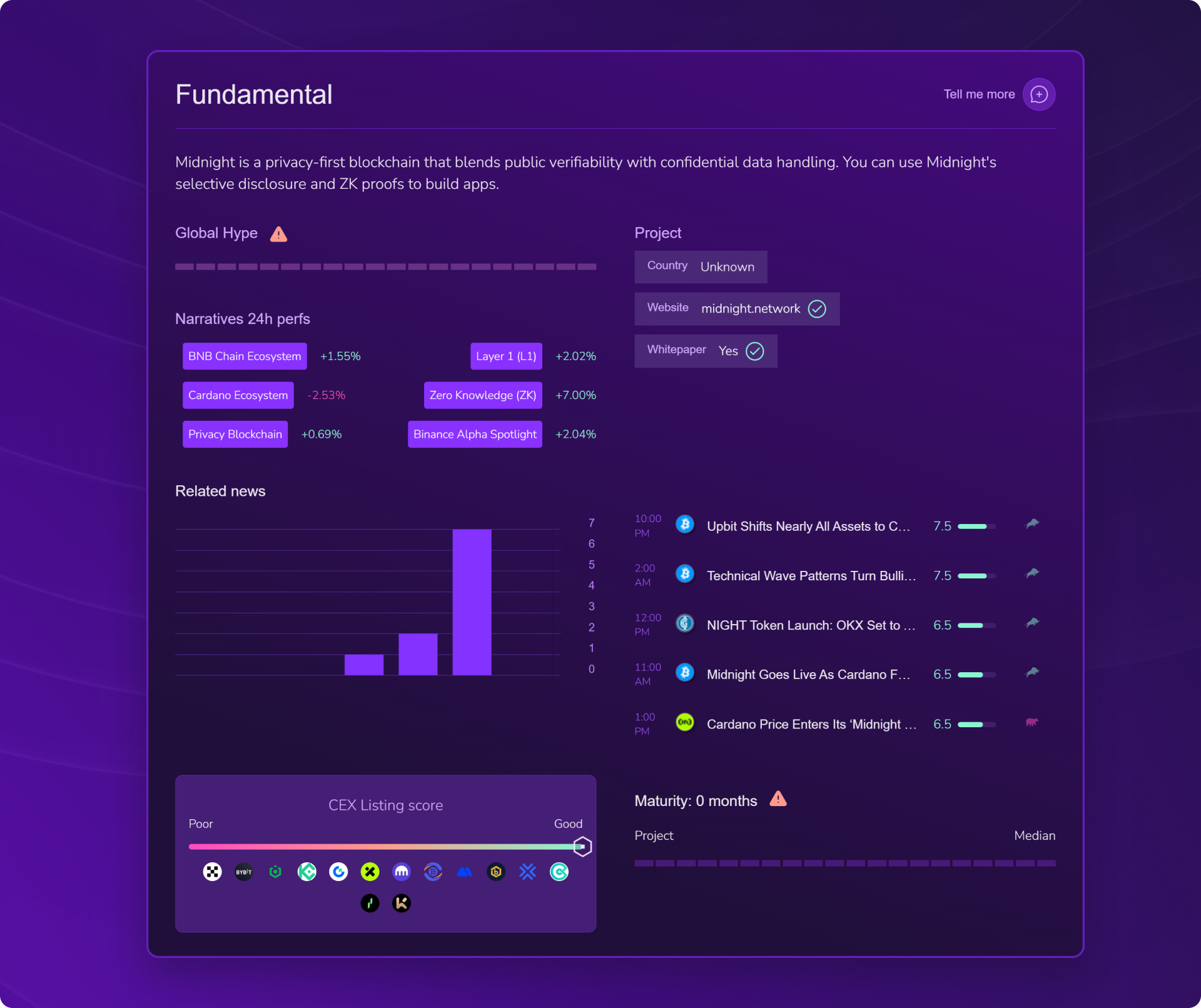
- Fundamental score: 64
- Maturity: 0 months
- Country: Unknown
- Whitepaper: Yes
- CEX Listing score: Good
👉 To explain simply: Midnight is an extremely recent project (launched in December 2024), which explains its 0-month maturity. Despite this, the fundamental score of 64 is encouraging for such a recent launch. The presence of a whitepaper and median CEX listing show a structured approach, even if the project still needs to prove itself over time. Charles Hoskinson's backing and strong narratives (privacy blockchain, ZK proofs) partially compensate for the lack of history.
Social analysis of Midnight ($NIGHT): solid engagement and active community
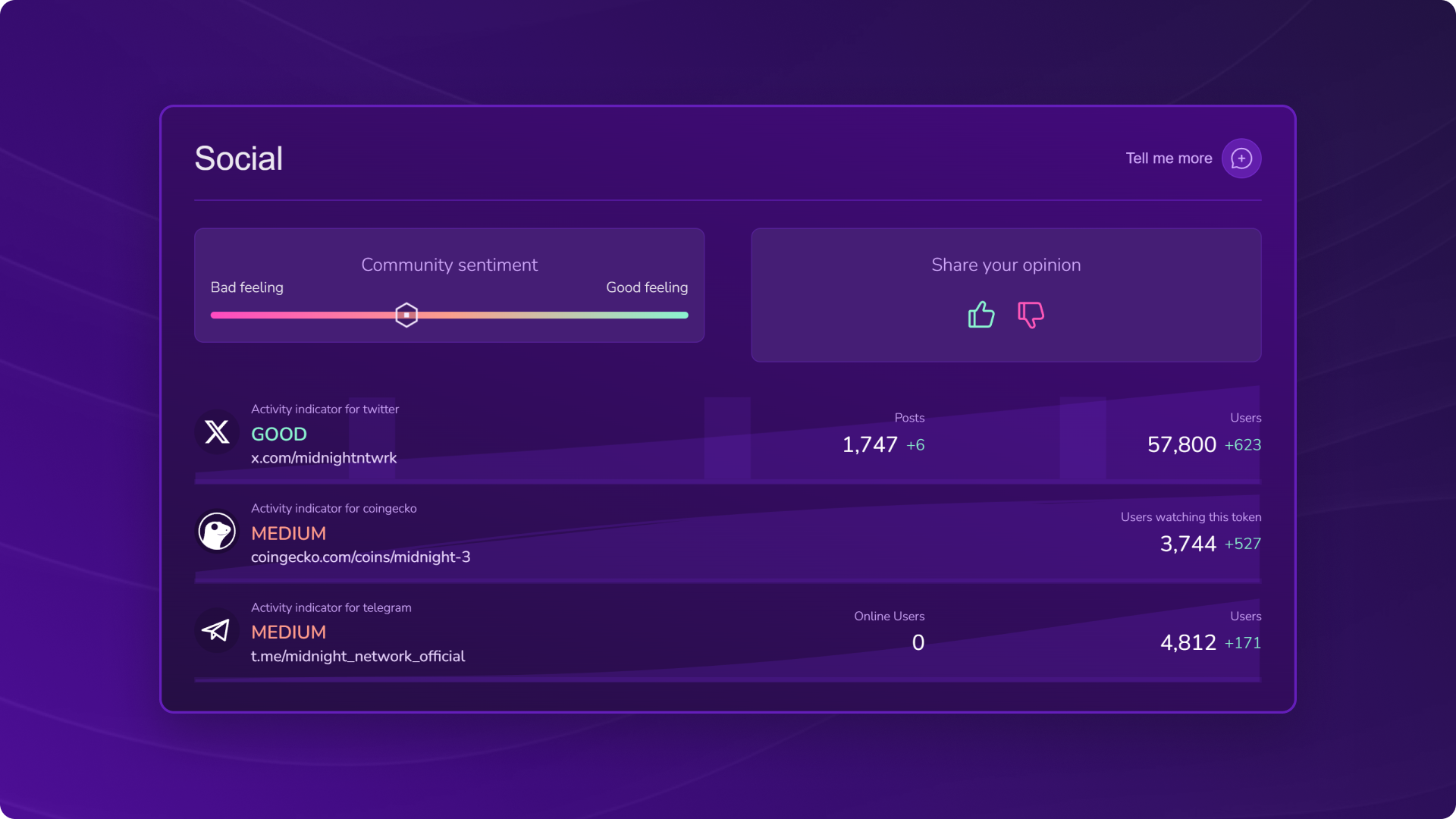
- Twitter: 1,747 posts – 57,800 users
- CoinGecko: 3,744 users watching $NIGHT
- Telegram: 4,812 members
- Community sentiment: neutral
👉 The community is growing steadily with excellent engagement on Twitter (almost 58,000 users) and nearly 3,700 watchlists on CoinGecko. The number of Telegram members is modest but growing. For such a recent project, these figures show promising traction. The neutral community sentiment is normal for a recent launch where investors are still in observation mode.
Cybersecurity of Midnight ($NIGHT): major concerning vulnerabilities
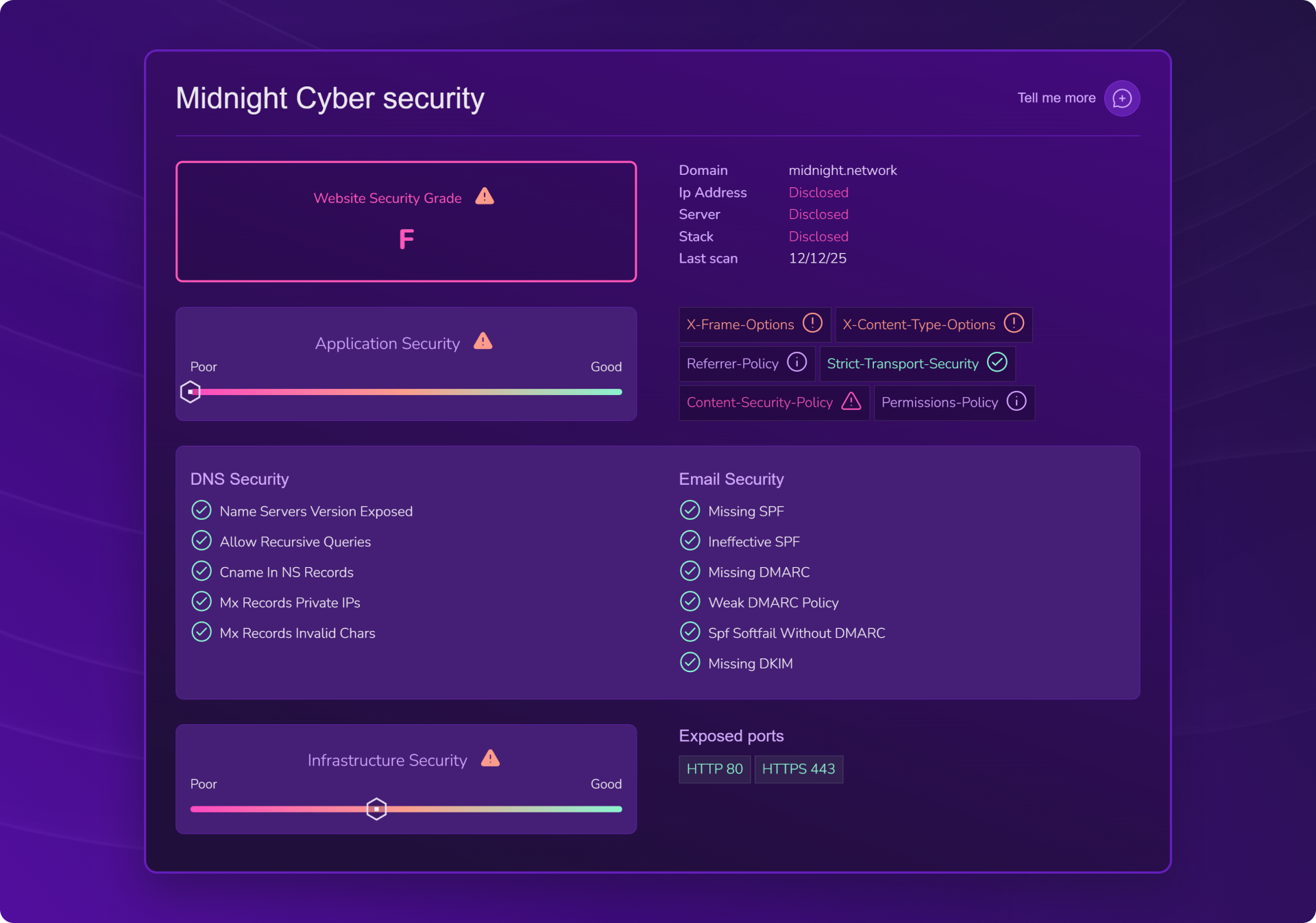
- Website security rating: F
Identified vulnerabilities:
- IP address disclosed
- Server disclosed
- Stack disclosed
- ⚠️ X-Frame-Options (clickjacking risk)
- ⚠️ X-Content-Type-Options (risk of executing unsecured content)
- ⚠️ Content-Security-Policy (risk of injected/malicious content)
👉 In simple terms: Midnight's cybersecurity is clearly insufficient with an F rating. The exposure of the IP address, server, and stack greatly facilitates malicious reconnaissance and opens the door to targeted attacks. The three major identified vulnerabilities directly expose users to clickjacking attacks, execution of malicious scripts, and injection of dangerous content. For a project that places privacy and security at the heart of its value proposition, this is deeply paradoxical and unacceptable. These critical flaws must be urgently corrected before any serious adoption.
Smart Contract audit of Midnight ($NIGHT): governance to monitor
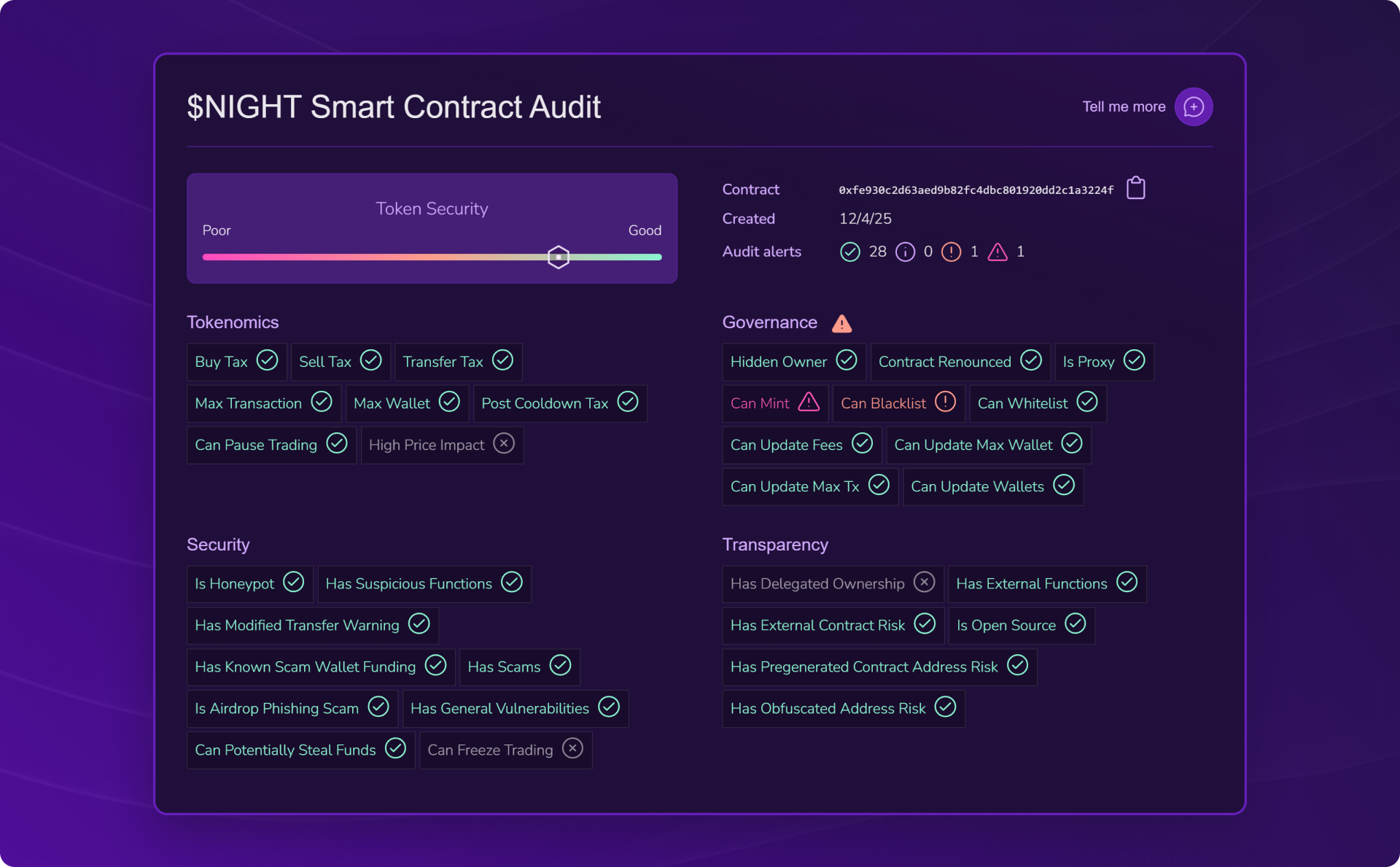
- ⚠️ Can blacklist addresses
- ⚠️ Can mint new tokens
👉 In clear terms: Midnight's smart contract presents two elements that require vigilance: the minting capability (creating new tokens) which could dilute value, and the ability to blacklist addresses which gives censorship power. These two functions reveal still-centralized governance that could be used arbitrarily. For a project that advocates privacy and decentralization, this centralization is a friction point to watch carefully.
On-chain data of Midnight ($NIGHT): recent deployment and notable concentration

- Total holders: 5,996
- Total transactions: 285,180
- Chains: 1 chain (BSC)
- Deployment and activity: Good
- Decentralization: High
👉 To summarize: For a project launched only a few weeks ago, Midnight shows remarkable on-chain activity with nearly 6,000 holders and 285,000 transactions. The deployment on BSC and the high judged decentralization are good signals. However, concentration in top wallets remains significant, even if the percentages displayed at 0% suggest relative distribution. Growth activity (+4,382 holders and +50,519 transactions in 24h) shows strong community engagement.
The verdict: strengths and weaknesses of Midnight ($NIGHT)
Strengths:
- Massive volume and solid liquidity
- Decent liquidity ratio
- Moderate future dilution
- Strong on-chain activity for a recent launch
- High judged decentralization
- Rapidly growing community and solid engagement
- Presence of a whitepaper
- Encouraging fundamental score of 64 for such a recent project
Weaknesses:
- Cybersecurity needs review, critical major flaws
- Centralized smart contract governance: Can Mint + Can Blacklist
- 0 months maturity, no operational history
Conclusion
Midnight ($NIGHT) presents a contrasted profile, as revealed by the Kryll X-Ray audit. On the financial and on-chain front, the project displays encouraging signals: massive volumes, a 69% liquidity ratio, as well as sustained on-chain activity, with nearly 6,000 holders and 285,000 transactions for such a recent launch. Decentralization is judged high and the community is experiencing rapid growth.
However, the audit highlights critical flaws: catastrophic cybersecurity rated F, exposure of IP, server and technical stack, three major web vulnerabilities, as well as strongly centralized smart contract governance (Can Mint, Can Blacklist). With 0 months of maturity, the project has no history to assess its reliability.
Why use X-Ray?
DYOR is good. DYOR with X-Ray is better. Here's why this tool will drastically change your approach to the crypto market:
- ⚡ Instant complete audit: Get a clear overview of a token in seconds: smart contract, on-chain data, financial metrics, and social signals all in one place.
- 🔐 Enhanced risk detection: X-Ray immediately spots warning signals: trapped contracts, unlimited mint, concentrated holders, or security flaws on the project's website.
- 🧭 Considerable time savings: No more endless hours of research: X-Ray centralizes all critical data in one click.
- 🗣️ Accessible to everyone: The intuitive interface, clear visuals, and simplified explanations make the audit understandable regardless of your level.
- 💬 AI integration: Ask a question to the Kryll³ AI Agent to trigger an audit or deepen a point, without even opening the interface. 100% conversational, as if you were talking to a crypto expert with infinite knowledge.
- 📚 Continuous learning: Explore data and develop your crypto skills with each use. Every audit is a lesson.
With all these cross-analyses, X-Ray offers much more than a simple glance: it's a true intelligent dashboard, designed so everyone can understand, compare, and decide without getting lost in complexity.
| Criteria | Manual Audit 😩 | Audit with X-Ray 😎 |
|---|---|---|
| Ease | Complex | ✅ Ultra-simple |
| Time spent | Several hours | ✅ A few minutes |
| Risks detected | Variable | ✅ Automatically listed |
| Number of tools needed | Several dozens | ✅ All-in-one in X-Ray |
| AI Agent integration | None | ✅ Integrated |
How to access X-Ray?
Want to audit a token or do a quick check before investing? The X-Ray module from Kryll³ is here to simplify your life. Here's how to access it in seconds:
- Go to the X-Ray tab on the Kryll³ platform
- Connect your Web3 wallet to unlock all X-Ray features (Don't have a Web3 wallet? Click here)
✅ You're now on X-Ray!
All you have to do is enter the name or address of a token to launch the complete analysis and get a clear and synthetic audit of the crypto of your choice.